Open source Waf security protection solution
After adding CDN to the website recently, there are always a lot of junk requests inexplicably in the early morning, some of which are scans, some are large model UserAgents, and some are black spiders.
In order to save CDN costs and prevent various injection attacks, I started to investigate open source Waf solutions (my own small broken site is enough). If it is used by an enterprise, it is recommended to use a commercial version, such as Alibaba Cloud’s DCDN, Tencent’s EdgeOne or overseas Cloudflare (the first choice for overseas business).
1. Function introduction
SafeLine is an open source Waf solution of Changting Technology. The core detection capability is driven by intelligent semantic analysis algorithms.
The main function is a network security gateway, focusing on Waf, which can defend against all Web attacks, such as sql injection, code injection, os command injection, CRLF injection, ldap injection, xpath injection, rce, xss, xxe, ssrf, path traversal, backdoor, brute force cracking, http flood, robot abuse, etc.
I took a look at the project source code. The API uses golang, and the core waf function uses tengine+Lua, which is similar to openresty.
Project address: https://github.com/chaitin/safeline
Official website address: https://waf-ce.chaitin.cn/
Note: Other popular gateways, such as Apisix, Kong, Openresty, etc.
2. Installation
Download offline image
Because many domestic dockerhub image accelerations are no longer available a few days ago, this can only be done offline.
Configuring the environment
| |
You need to initialize the administrator account when you log in to Leichi for the first time. Just execute the following command
| |
After the command is executed, the password of the admin account will be randomly reset. The output result is as follows
The basic installation is completed here. You only need to open the 9443 port access through the cloud ACL
You can open a browser to visit https://
3. Website configuration
SSL certificate configuration:
Supports custom uploaded certificates and application for free certificates.
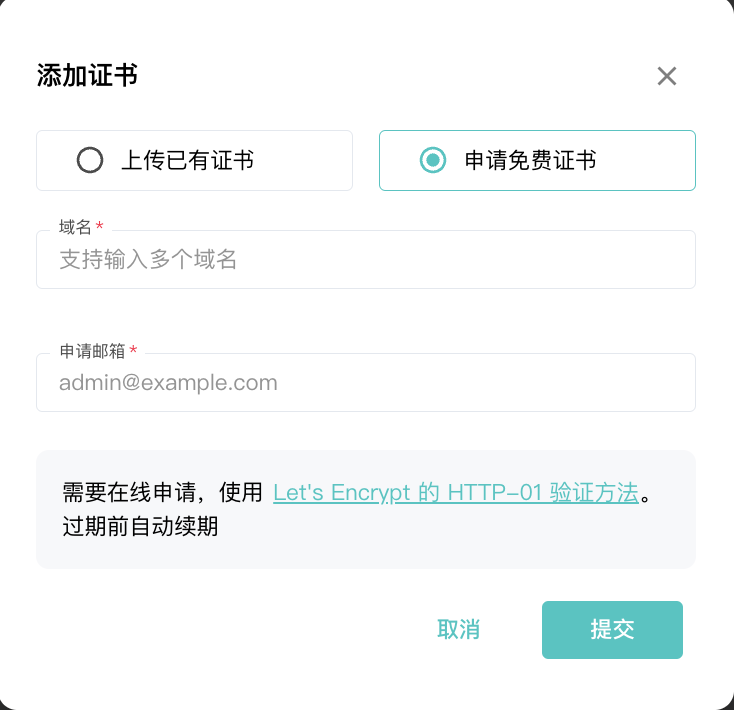
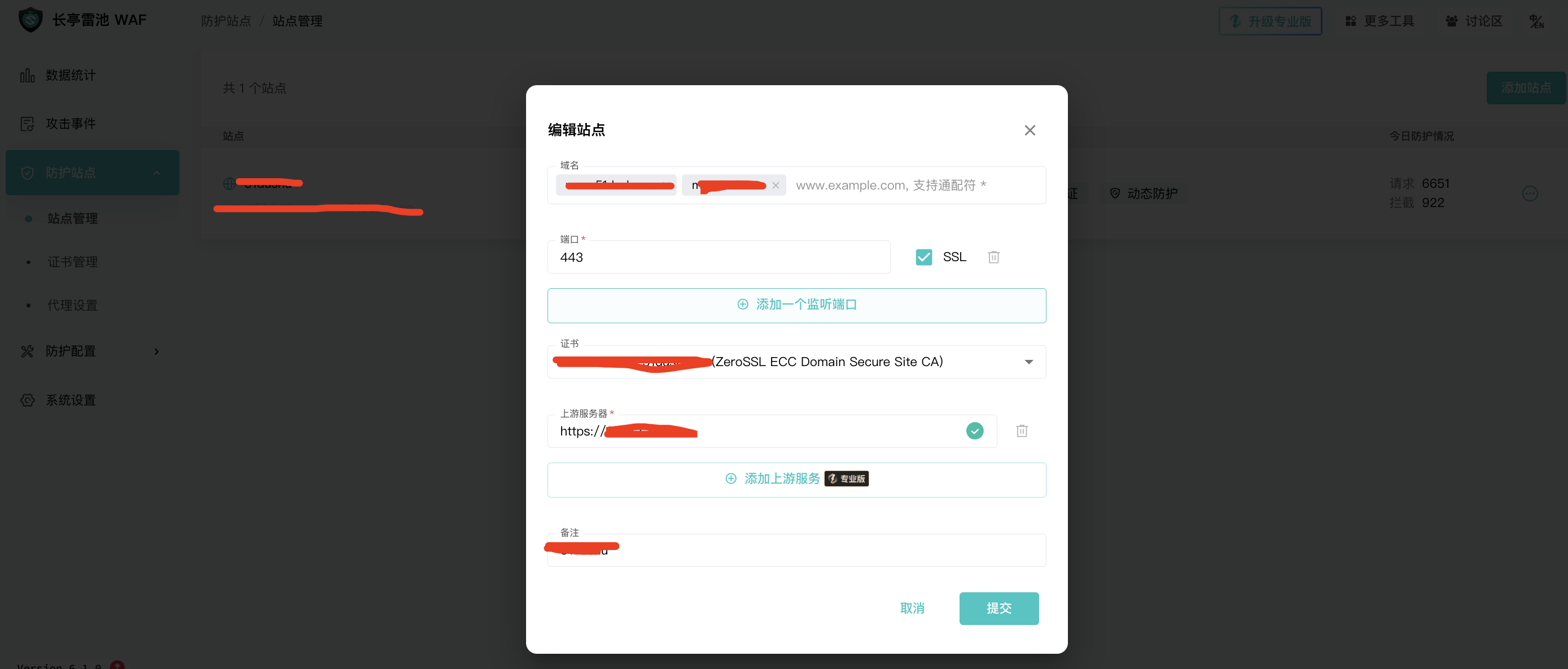
Add site:
Add site. In addition, human-machine verification, identity verification, and dynamic protection are enabled by default. It should be noted that when adding upstream servers here, the back-to-source is vague, such as the back-to-source port configuration, protocol, etc.
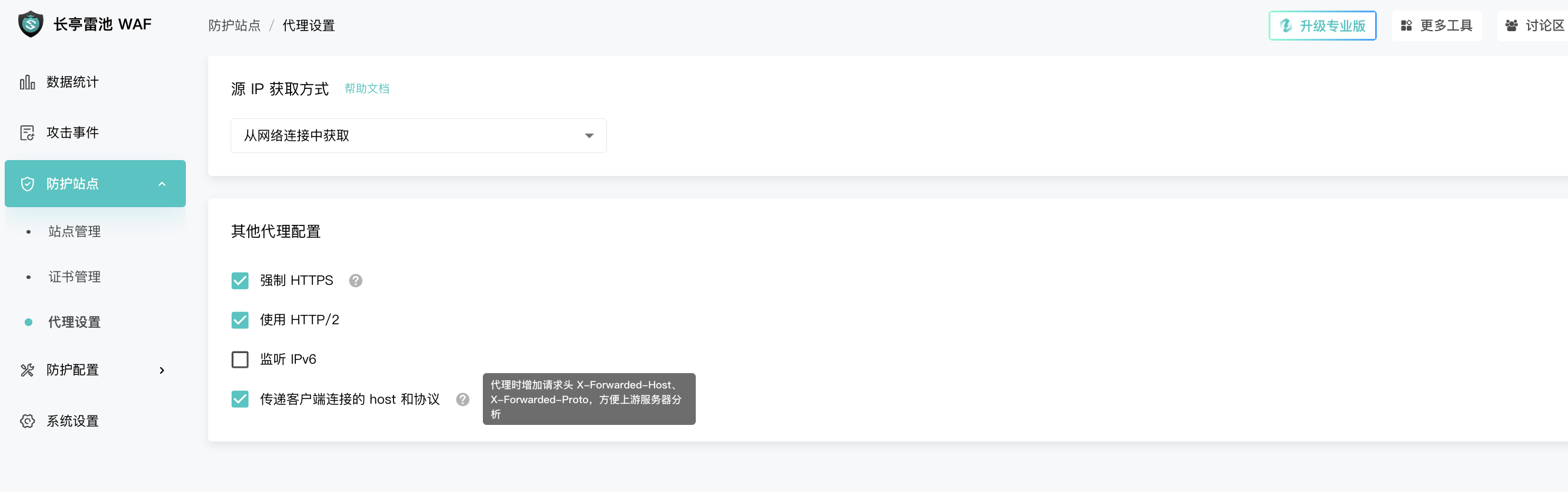
Proxy configuration:
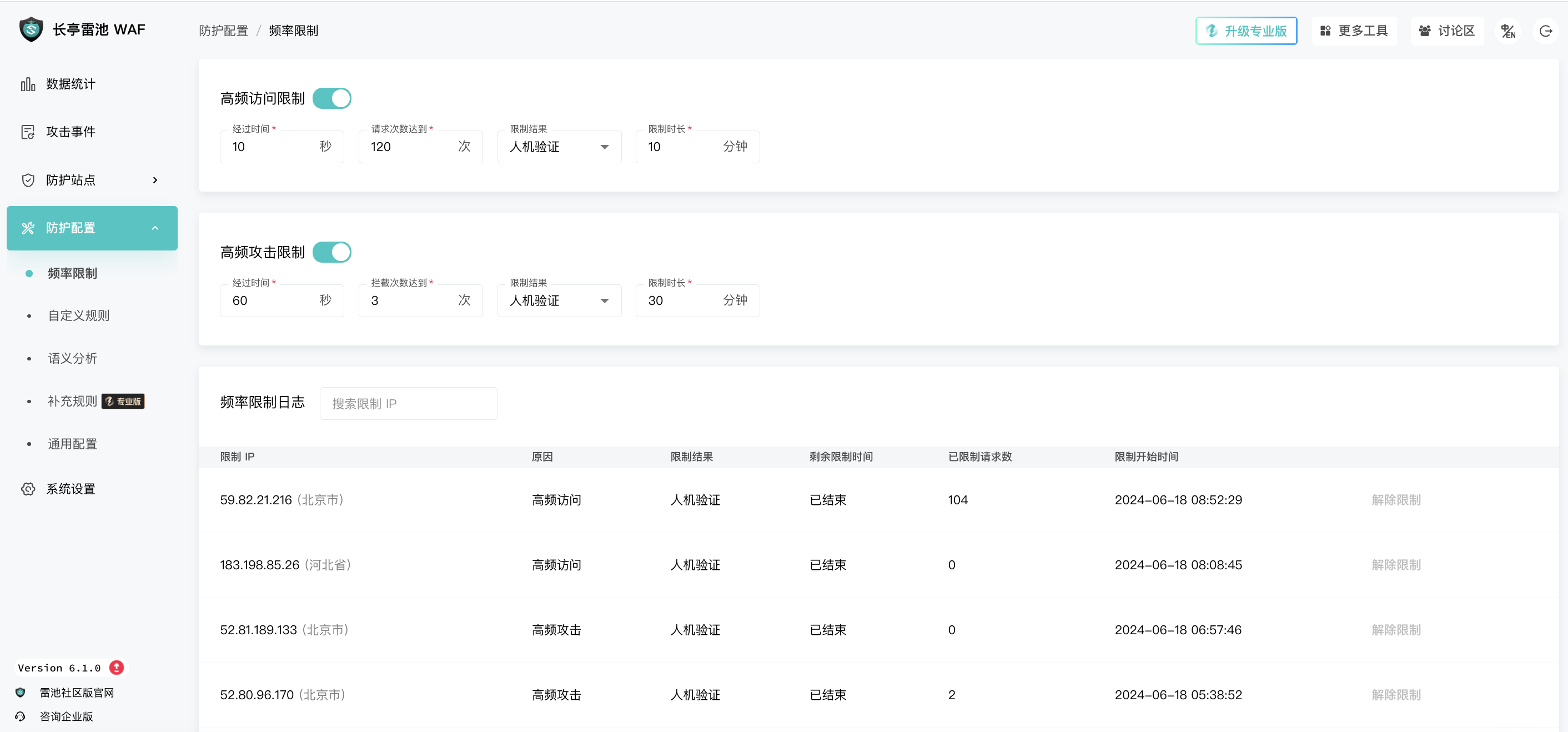
Security protection settings:
Here mainly configure frequency limit (similar to nginx limit), custom rules (set rules according to http header information), semantic analysis (injection related), etc.
Limit access frequency: underlying logic and limit_req, limit_conn, limit_rate under nginx Almost
Custom rules: mainly make some strategies based on http header information, similar to the access control of common CDN, but this function is more flexible.
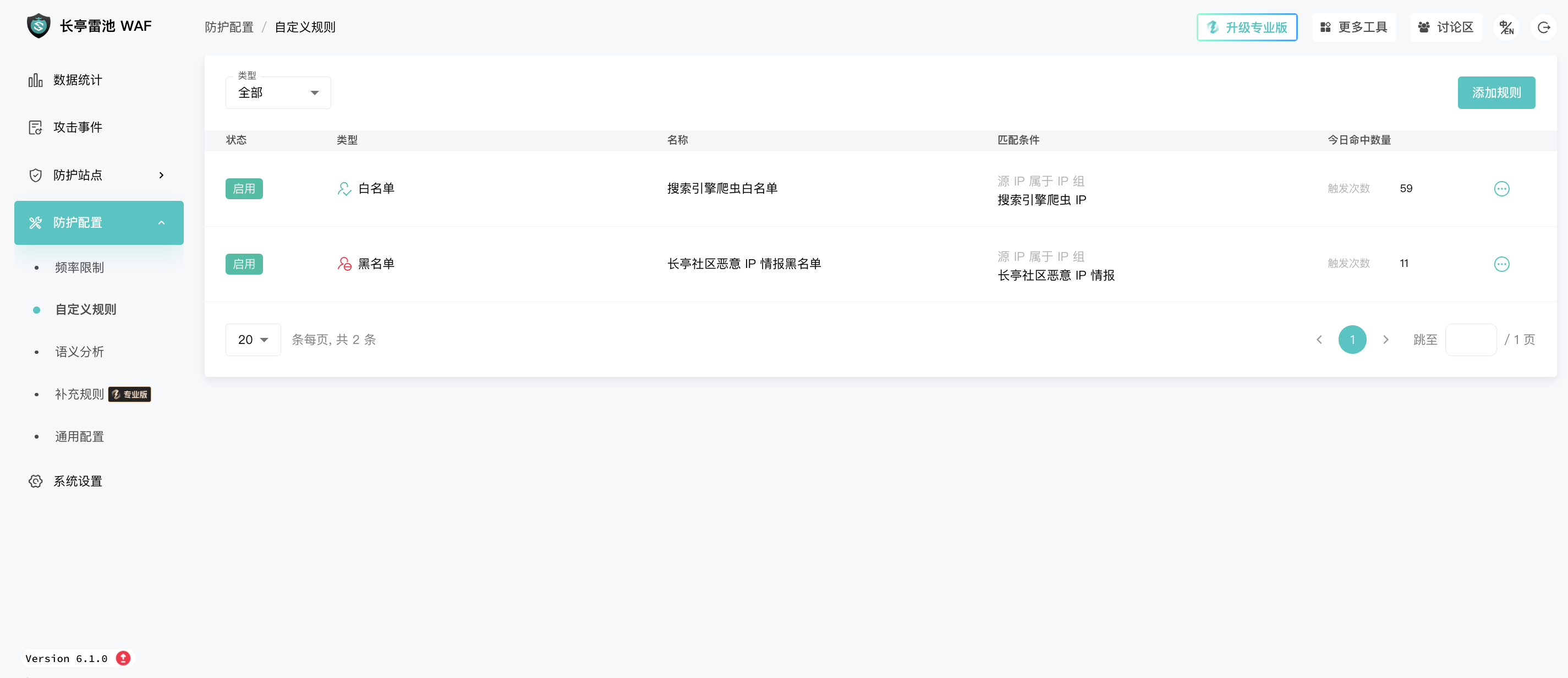
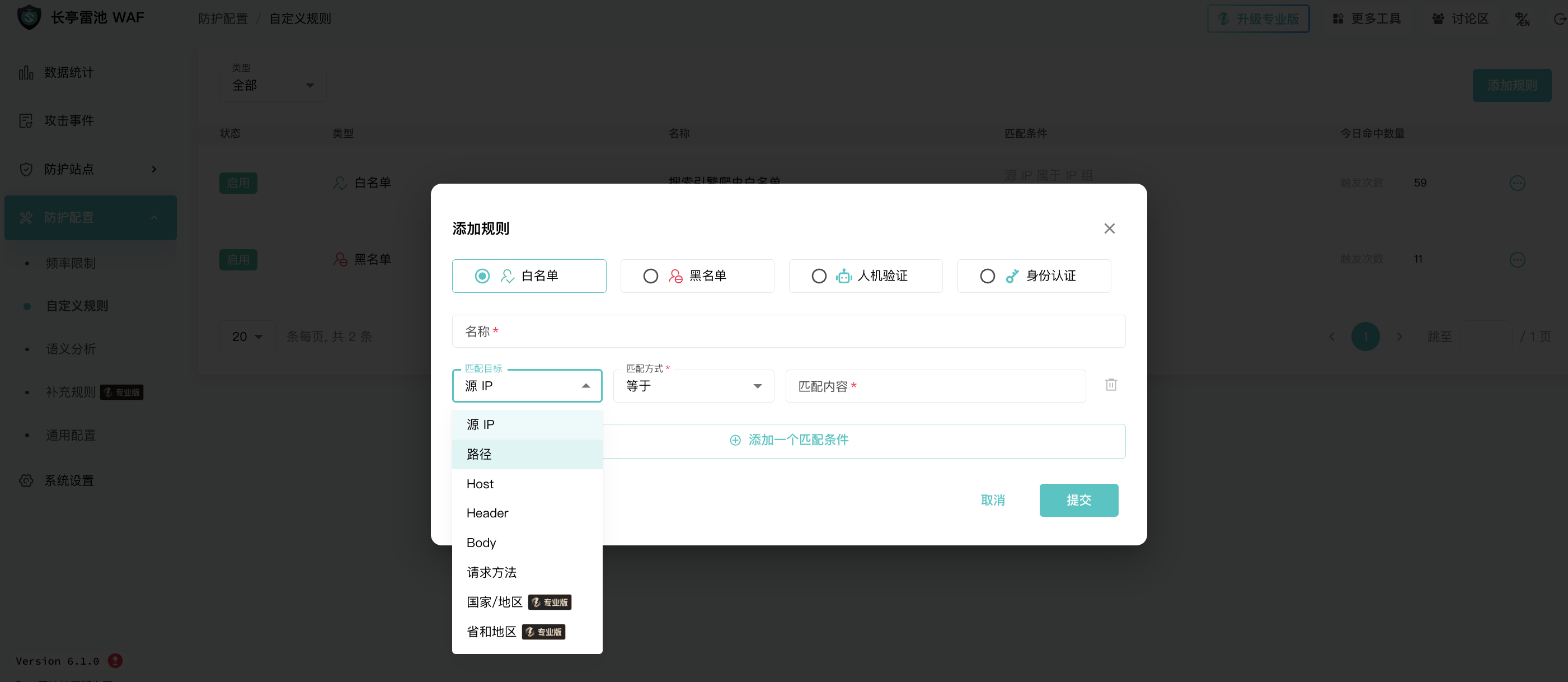
Semantic analysis: mainly identifies various injections, robot detection, etc.
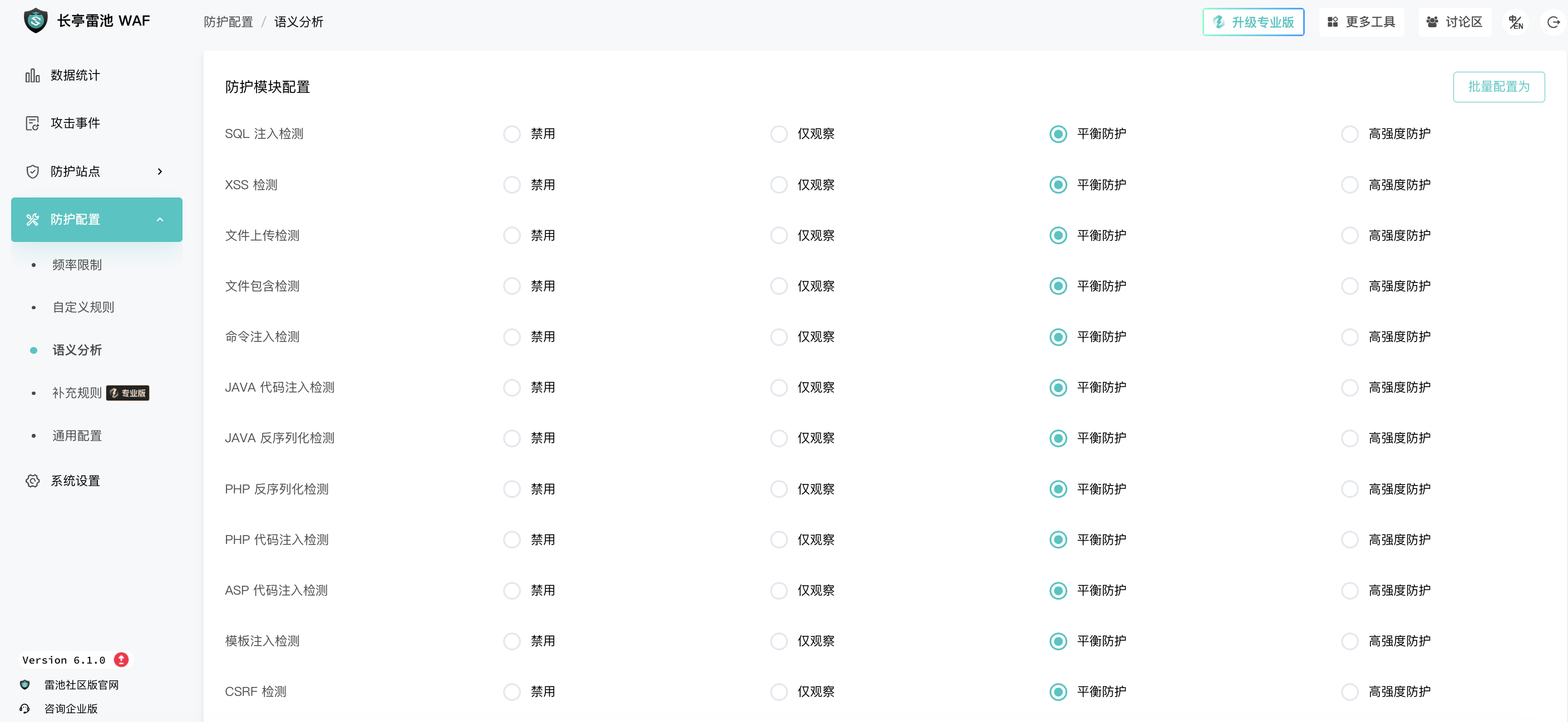
4. Summary
After two days of testing, Leichi basically meets the needs of my small broken site, but it also has many places that cannot be met.
For example: applying for a free certificate does not support wildcard domain names, upstream server source protocol is ambiguous, etc.
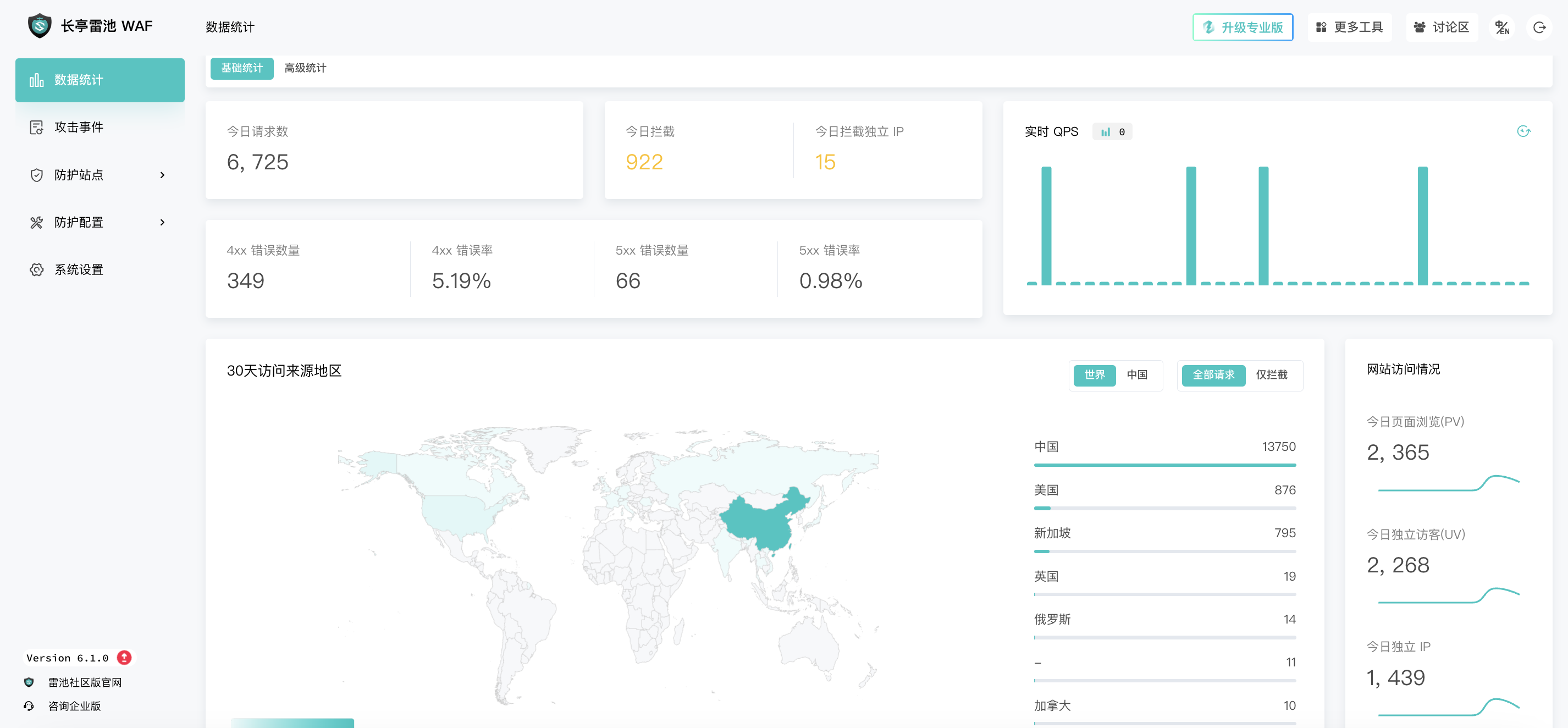
Finally, here is a rendering.
Reference: https://docs.waf-ce.chaitin.cn/zh/home